See which JavaScript commands are injected through an in-app browser
Last week I published a report on the risks of mobile apps using embedded browsers. Some apps, like Instagram and Facebook, inject JavaScript code into third-party websites, which poses potential security and privacy risks to the user.
I was so happy to see that the article featured by major news outlets around the world, like TheGuardian and The Register, got over a million impressions on Twitter and was ranked #1 on HackerNews for more than 12 hours. After reading the replies and DMs, I saw a common question in the community:
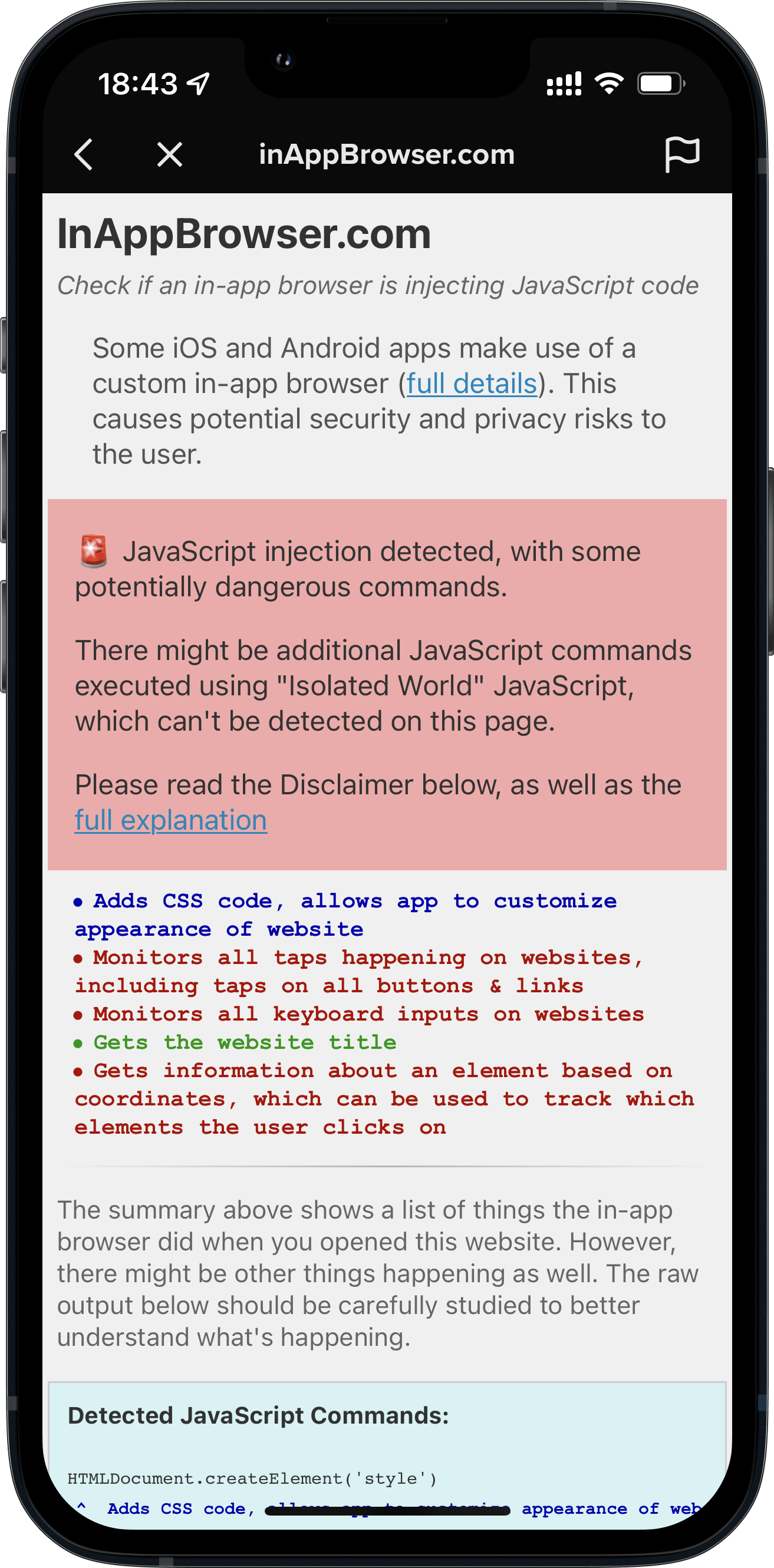 TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
"How can I check what apps are doing in their webviews?"
Introducing InAppBrowser.com, a simple tool for listing JavaScript commands executed by the iOS app rendering the page.
To try this tool yourself:
Open an app you want to analyze Share the https://InAppBrowser.com URL somewhere in the app (e.g. send a DM to a friend or post to your feed) Tap the link in the app to open it Read the report on screen TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
I started using this tool to analyze the most popular iOS apps that have their own built-in browser. Here are the results I found.
For this analysis, I excluded all third-party iOS browsers (Chrome, Brave, etc.) because they use JavaScript to provide some of their functionality, such as a password manager. Apple requires all third-party apps in iOS browsers to use the Safari WebKit rendering engine.
Important Note: This tool cannot detect all executed JavaScript commands, and does not show any tracking that the app might be doing using native code (such as gesture recognition personalized). More on that below.
Fully open-source
InAppBrowser.com is designed so that anyone can see for themselves what apps are doing in their built-in browsers. I decided to open the code used for this analysis, you can check it on GitHub. This allows the community to update and improve this script over time.
iOS apps that have their own in-app browser Option to open in default browser: Does the app provide a button to open the currently displayed link in the default browser? Edit Page: Does the app inject JavaScript code into third-party websites to edit its content? This includes adding tracking code (like entries, text selects, taps, etc.), injecting external JavaScript files, as well as creating new HTML elements. Retrieve Metadata: Does the app run JavaScript code to retrieve metadata from the website? It's a harmless thing to do and doesn't cause any real security or privacy risk. JS: A link to the JavaScript code that I was able to detect. Disclaimer: Other code may be running. The code may not be a 100% accurate representation of all JS commands.Click the

Last week I published a report on the risks of mobile apps using embedded browsers. Some apps, like Instagram and Facebook, inject JavaScript code into third-party websites, which poses potential security and privacy risks to the user.
I was so happy to see that the article featured by major news outlets around the world, like TheGuardian and The Register, got over a million impressions on Twitter and was ranked #1 on HackerNews for more than 12 hours. After reading the replies and DMs, I saw a common question in the community:
 TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
"How can I check what apps are doing in their webviews?"
Introducing InAppBrowser.com, a simple tool for listing JavaScript commands executed by the iOS app rendering the page.
To try this tool yourself:
Open an app you want to analyze Share the https://InAppBrowser.com URL somewhere in the app (e.g. send a DM to a friend or post to your feed) Tap the link in the app to open it Read the report on screen TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
TikTok's in-app browser injects code to observe all keystrokes and keystrokes, which can include passwords and credit cards
I started using this tool to analyze the most popular iOS apps that have their own built-in browser. Here are the results I found.
For this analysis, I excluded all third-party iOS browsers (Chrome, Brave, etc.) because they use JavaScript to provide some of their functionality, such as a password manager. Apple requires all third-party apps in iOS browsers to use the Safari WebKit rendering engine.
Important Note: This tool cannot detect all executed JavaScript commands, and does not show any tracking that the app might be doing using native code (such as gesture recognition personalized). More on that below.
Fully open-source
InAppBrowser.com is designed so that anyone can see for themselves what apps are doing in their built-in browsers. I decided to open the code used for this analysis, you can check it on GitHub. This allows the community to update and improve this script over time.
iOS apps that have their own in-app browser Option to open in default browser: Does the app provide a button to open the currently displayed link in the default browser? Edit Page: Does the app inject JavaScript code into third-party websites to edit its content? This includes adding tracking code (like entries, text selects, taps, etc.), injecting external JavaScript files, as well as creating new HTML elements. Retrieve Metadata: Does the app run JavaScript code to retrieve metadata from the website? It's a harmless thing to do and doesn't cause any real security or privacy risk. JS: A link to the JavaScript code that I was able to detect. Disclaimer: Other code may be running. The code may not be a 100% accurate representation of all JS commands.Click the
What's Your Reaction?














![Three of ID's top PR executives quit ad firm Powerhouse [EXCLUSIVE]](https://variety.com/wp-content/uploads/2023/02/ID-PR-Logo.jpg?#)







