Getting kernel code running on an MTE-enabled Pixel 8
In This job, I will look has CVE-2023-6241, A vulnerability In THE Arm Mali GPU that I reported has Arm on November 15, 2023 And was fixed In THE Arm Mali driver version r47p0, which was released publicly on December 14, 2023. He was fixed In Android In THE March security update. When exploited, This vulnerability allow A malicious Android application has earn arbitrary core coded execution And root on THE device. THE vulnerability affected devices with more recent Arm Mali GPU that to use THE Order Flow Front end (CSF) functionality, such as that of Google Pixels 7 And Pixels 8 Telephone (s. What East interesting about This vulnerability East that he East A logic bug In THE memory management unit of THE Arm Mali GPU And he East able of get around Memory Marking Extension (MTE), A new And powerful mitigation against memory Corruption that was First of all supported In Pixels 8. In This job, I will to show how has to use This bug has earn arbitrary core coded execution In THE Pixels 8 Since A unreliable user application. I to have confirmed that THE exploit works with success even with core MTE activated by following these instructions.
Bras64 MTEMTE East A very GOOD documented functionality on more recent Arm processors that uses material implementations has check For memory Corruption. As there are Already a lot GOOD articles about MTE, I will only briefly go through THE idea of MTE And explain It is importance In comparison has other mitigations For memory Corruption. Readers WHO are interested In more details can, For example, to consult This article And THE white paper released by Arm.
While THE Bras64 architecture uses 64 little pointers has to access memory, there East generally No need has to use such A big address space. In practical, most apps to use A a lot smaller address space (generally 52 parts Or less). This leaves THE The highest parts In A needle unused. THE main idea of memory marking East has to use these upper parts In A address has store A "label" that can SO be used has check against THE other label stored In THE memory block partner with THE address. THE help has mitigate common types of memory corruption as follows:
In THE case of A linear overflow, A needle East used has dereferencing A adjacent memory block that has A different label compared with has THE A stored In THE needle. By verification these Keywords has dereferencing time, THE corrupt dereferencing can be detected. For use after release type memory corruption, as long as THE label In A memory block East erased each time he East released And A new label reassigned When he East assigned, dereferencing A Already released And recovered object will Also lead has A divergence between needle label And THE label In memory, which allow use after release has be detected.
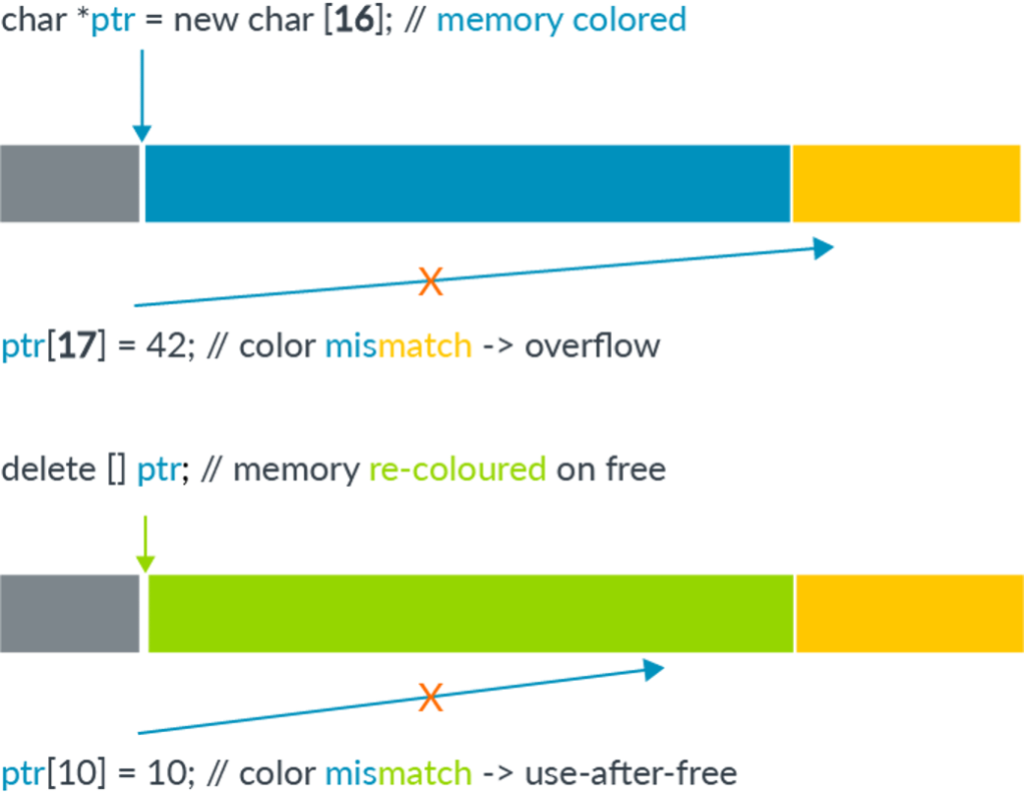
(THE above picture East Since Memory Marking Extension: Improve memory security through architecture published by Arm.)
THE main reason that memory marking East different Since previous mitigations, such as Core Control To flow Integrity (kCFI) East that, contrary to other mitigations, which disturbed later steps of A exploit, MTE East A very early scene mitigation that try has catch memory Corruption When he First of all arrived. As such, he East able has stop A exploit In A very early St...
In This job, I will look has CVE-2023-6241, A vulnerability In THE Arm Mali GPU that I reported has Arm on November 15, 2023 And was fixed In THE Arm Mali driver version r47p0, which was released publicly on December 14, 2023. He was fixed In Android In THE March security update. When exploited, This vulnerability allow A malicious Android application has earn arbitrary core coded execution And root on THE device. THE vulnerability affected devices with more recent Arm Mali GPU that to use THE Order Flow Front end (CSF) functionality, such as that of Google Pixels 7 And Pixels 8 Telephone (s. What East interesting about This vulnerability East that he East A logic bug In THE memory management unit of THE Arm Mali GPU And he East able of get around Memory Marking Extension (MTE), A new And powerful mitigation against memory Corruption that was First of all supported In Pixels 8. In This job, I will to show how has to use This bug has earn arbitrary core coded execution In THE Pixels 8 Since A unreliable user application. I to have confirmed that THE exploit works with success even with core MTE activated by following these instructions.
Bras64 MTEMTE East A very GOOD documented functionality on more recent Arm processors that uses material implementations has check For memory Corruption. As there are Already a lot GOOD articles about MTE, I will only briefly go through THE idea of MTE And explain It is importance In comparison has other mitigations For memory Corruption. Readers WHO are interested In more details can, For example, to consult This article And THE white paper released by Arm.
While THE Bras64 architecture uses 64 little pointers has to access memory, there East generally No need has to use such A big address space. In practical, most apps to use A a lot smaller address space (generally 52 parts Or less). This leaves THE The highest parts In A needle unused. THE main idea of memory marking East has to use these upper parts In A address has store A "label" that can SO be used has check against THE other label stored In THE memory block partner with THE address. THE help has mitigate common types of memory corruption as follows:
In THE case of A linear overflow, A needle East used has dereferencing A adjacent memory block that has A different label compared with has THE A stored In THE needle. By verification these Keywords has dereferencing time, THE corrupt dereferencing can be detected. For use after release type memory corruption, as long as THE label In A memory block East erased each time he East released And A new label reassigned When he East assigned, dereferencing A Already released And recovered object will Also lead has A divergence between needle label And THE label In memory, which allow use after release has be detected.

(THE above picture East Since Memory Marking Extension: Improve memory security through architecture published by Arm.)
THE main reason that memory marking East different Since previous mitigations, such as Core Control To flow Integrity (kCFI) East that, contrary to other mitigations, which disturbed later steps of A exploit, MTE East A very early scene mitigation that try has catch memory Corruption When he First of all arrived. As such, he East able has stop A exploit In A very early St...
What's Your Reaction?














![Three of ID's top PR executives quit ad firm Powerhouse [EXCLUSIVE]](https://variety.com/wp-content/uploads/2023/02/ID-PR-Logo.jpg?#)







