This week in security: Exchange 0-day, Doppelgangers and Python stand out in TAR
According to GTSC researchers, there is an unpatched 0-day used in the wild to exploit fully patched Microsoft Exchange servers. When they found a compromised server, they reported to Microsoft through ZDI, but after finding several compromised Exchange servers, they raised alarm bells for everyone. It appears to be a similar attack to ProxyShell, in that it uses the Autodiscover endpoint as a starting point. They suspect that a Chinese group is using the exploit, based on some of the indicators found in the webshell that is installed.
There is a temporary mitigation, adding a URL-based query block on the .*autodiscover\.json.*\@.*Powershell string. Exact details are available in the article. If you're using Exchange with IIS, this should probably be added to your system now. Then use the automated tool or run the PowerShell one-liner to detect the compromise: Get-ChildItem -Recurse -Path -Filter "*.log" | Select-String -Pattern 'powershell.*autodiscover\.json.*\@.*200. This one has the potential to be another really nasty problem, and can be deworming. As of this writing, this is an open, unfixed issue in Microsoft Exchange. Come back and finish the rest of this article after securing your systems.
The digital doppelgangers[Connor Tumbleson] got a weird surprise a few weeks ago, via an email from another developer, [Andrew], who had been hired to impersonate [Connor] for an interview. hiring. Say what? This scam is new to us and appears to go like this: The scammer chooses a GitHub account with a professional photo and impressive activity, then creates an Upwork account in that senior developer's name. This includes a thorough analysis of publicly available data on the target developer. Then our scammer contacts another GitHub account holder, with less impressive credentials - a junior developer, and makes a job offer: working with a non-English speaking development team, doing development work and work as the face of the team when working with North American clients. The only questionable part of the job is that the new recruit will conduct interviews using the name of his teammates.
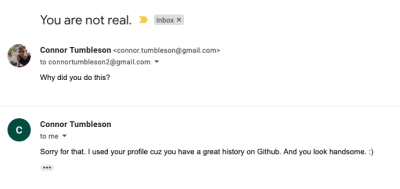
That brings us to [Andrew], who was the "junior developer" in this scenario. Everything seemed legit, until he realized the team member he was supposed to be representing wasn't actually on the team, and contacted the real [Connor], who started to dig.
It boils down to an employment scam, trying to use the name and reputation of a qualified developer to land a contract. Keep an eye out for fake profiles on Upwork or similar job boards. And if you get an offer that looks like the one that bit [Andrew], beware. And finally, if you hired a developer through Upwork, ask yourself if you really confirmed that your new developer is who he claims to be.
Changing Byte Python times in the TARFor this bug, what we're going to do here is go back, very far, back in time. CVE-2001-1267 was the original tar directory traversal vulnerability. You could inc...

According to GTSC researchers, there is an unpatched 0-day used in the wild to exploit fully patched Microsoft Exchange servers. When they found a compromised server, they reported to Microsoft through ZDI, but after finding several compromised Exchange servers, they raised alarm bells for everyone. It appears to be a similar attack to ProxyShell, in that it uses the Autodiscover endpoint as a starting point. They suspect that a Chinese group is using the exploit, based on some of the indicators found in the webshell that is installed.
There is a temporary mitigation, adding a URL-based query block on the .*autodiscover\.json.*\@.*Powershell string. Exact details are available in the article. If you're using Exchange with IIS, this should probably be added to your system now. Then use the automated tool or run the PowerShell one-liner to detect the compromise: Get-ChildItem -Recurse -Path -Filter "*.log" | Select-String -Pattern 'powershell.*autodiscover\.json.*\@.*200. This one has the potential to be another really nasty problem, and can be deworming. As of this writing, this is an open, unfixed issue in Microsoft Exchange. Come back and finish the rest of this article after securing your systems.
The digital doppelgangers[Connor Tumbleson] got a weird surprise a few weeks ago, via an email from another developer, [Andrew], who had been hired to impersonate [Connor] for an interview. hiring. Say what? This scam is new to us and appears to go like this: The scammer chooses a GitHub account with a professional photo and impressive activity, then creates an Upwork account in that senior developer's name. This includes a thorough analysis of publicly available data on the target developer. Then our scammer contacts another GitHub account holder, with less impressive credentials - a junior developer, and makes a job offer: working with a non-English speaking development team, doing development work and work as the face of the team when working with North American clients. The only questionable part of the job is that the new recruit will conduct interviews using the name of his teammates.

That brings us to [Andrew], who was the "junior developer" in this scenario. Everything seemed legit, until he realized the team member he was supposed to be representing wasn't actually on the team, and contacted the real [Connor], who started to dig.
It boils down to an employment scam, trying to use the name and reputation of a qualified developer to land a contract. Keep an eye out for fake profiles on Upwork or similar job boards. And if you get an offer that looks like the one that bit [Andrew], beware. And finally, if you hired a developer through Upwork, ask yourself if you really confirmed that your new developer is who he claims to be.
Changing Byte Python times in the TARFor this bug, what we're going to do here is go back, very far, back in time. CVE-2001-1267 was the original tar directory traversal vulnerability. You could inc...
What's Your Reaction?














![Three of ID's top PR executives quit ad firm Powerhouse [EXCLUSIVE]](https://variety.com/wp-content/uploads/2023/02/ID-PR-Logo.jpg?#)







